- What Is Prodiscover Basic
- Prodiscover Basic Forensics Software
- Prodiscover Basic Edition
- Prodiscover Basic Features
ProDiscover Forensics or ProDiscover Incident Response is a powerful information security tool that enables computer forensics professionals to find all of the digital information on a computer disk and subsequently protect digital evidence and produces good evidentiary reports for use in legal proceedings.ProDiscover Forensics or ProDiscover. ProDiscover Basic edition is the free member of the ProDiscover family for hard disk security examination. It may not be as comprehensive as the other two products in the family, but it will give you an idea of the great potential these suite of products have.
What You Need for This Project
- A Windows machine, real or virtual. I did it on the Mac in a VMware Fusion virtual machine running 32-bit Windows 7 Pro.
- Your Windows machine needs to have either Microsoft Wordor Open Office installed. If you don't have it,get Open Office here:
Downloading ProDiscover Basic Edition
In your Windows machine, open a Web browser and go toAt the bottom of the page, click the'Download ProDiscover Basic Edition (Version 8.2.0.5)'link. It's a free product and 73 MB in size. I used the 32-bit version, but you can try the 64-bit version if you like.
Installing ProDiscover
On your Windows desktop,right-clickthe ProDiscoverRelease8205Basic.zip file andclick 'Extract All...', Extract.Right-click the ProDiscoverRelease8205Basic.exe fileand click 'Run as Administrator'.
Click through the installer as usual to install the software.
Downloading a Sample Disk Image
In your Windows machine, in a Web browser, downloadthis file:This is an image of a 10 MB hard disk partition which contains several active files and several deleted files. The file is 418 KB in size.
Save the file on your desktop.
On your Windows desktop,right-clickthe p15.zip file andclick 'Extract All...', Extract.
Starting ProDiscover Basic
On your desktop, double-click the'ProDiscover Basic' icon.In the 'Launch Dialog' box, enter a'Project Number' of 15 and a'Project File Name' of 15-YOURNAME,replacing 'YOURNAME' with your own name,as shown below:
Click Open.
This creates a Project, but so far the Project has noevidence in it.
Adding an Image File
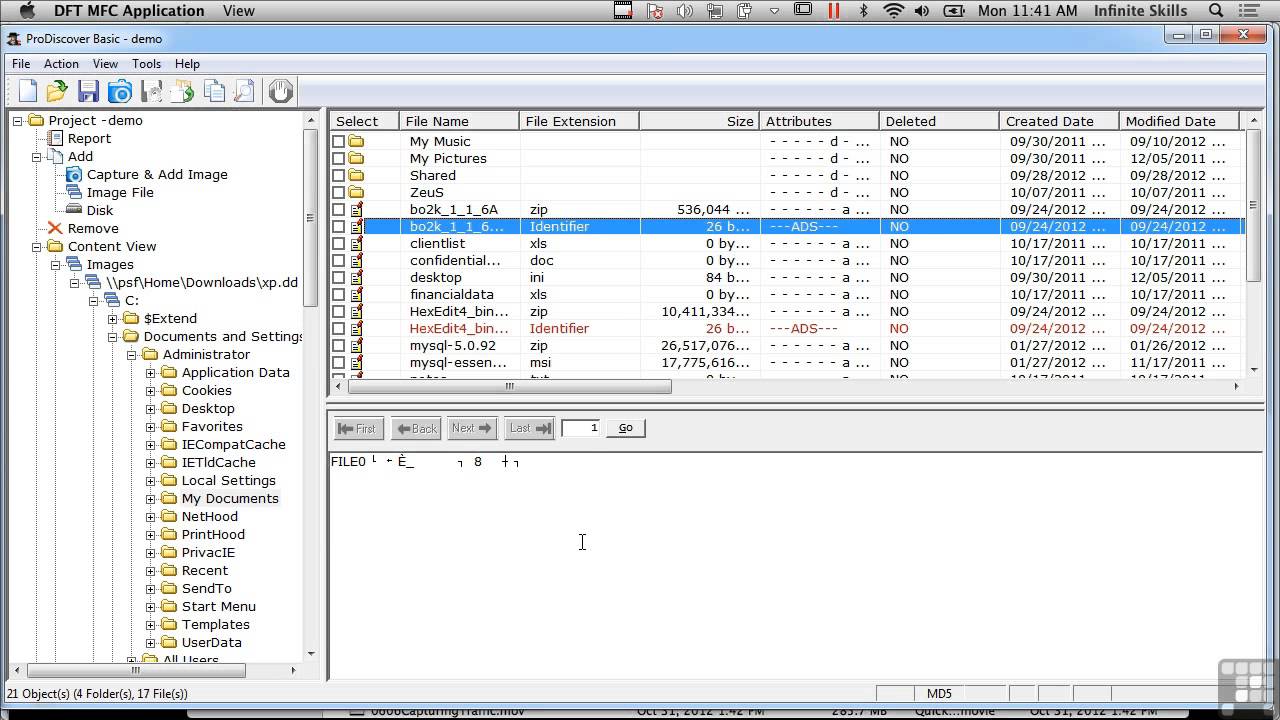
From the ProDiscover menu bar, clickAction, Add,'Image File...',as shown below. (This refers to a forensichard disk image, not a visible image likeJPG or GIF.)Navigate to your desktop,double-click the p15folder, anddouble-click the p15.ddfile.
Viewing the Hard Drive Image in Content View
In the left pane of ProDiscover, in the'Content View' section, click the plus signto expandImages.Expand C:UsersstudentDesktopp15p15.dd
Double-click C:
The contents of C: are displayed,as shown below.
Notice these items:
- In the left pane, a tree-structured list of thecontents of C appears.
- $Extend and 'System VolumeInformation' contain NTFSfile system data, which would be tedious toanalyze. Most of the time you don't haveto bother to analyze it--that's what ProDiscoverdoes for you.
- $RECYCLE.BIN contains files in the Recycle Bin, as you might guess.
- 'Deleted Files' contains files that were deleted, but are still recoverable by ProDiscover. As you will see, ProDiscover can't recover all of them.
- The upper right pane shows all the files in theroot of C:. Notice that there are three filesat the bottom with file extensions--these arethe active files (not deleted).
Viewing a DOCX File
In the upper right-pane of ProDiscover,click bill-of-rights.The lower right pane displays the file contentsin ASCII, as shown below. Since this is a .docx file, thecontents are not easy to read in this form.
In the upper right-pane of ProDiscover,double-click bill-of-rights.
If you have Microsoft Word or Open Office installed,the file will open in the appropriate applicationand become readable, as shown below.
If you don't have it, get Open Office here:
Saving a Screen Image
Make sure your screen shows these two items:- YOUR NAME in the title bar of ProDiscover
- Amendment I followed by readable text inMicrosoft Word or Open Office Writer
Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE TO GET FULL CREDIT!
Open Paint and paste in the image.
Save the image with the filename 'Your Name Proj 15a'. Use your real name, not the literal text 'Your Name'.
Viewing JPG files
In the upper right-pane of ProDiscover,double-click images. A visiblephoto of a kitten appears in 'Windows PhotoViewer' or some other image viewer.
images. A visiblephoto of a kitten appears in 'Windows PhotoViewer' or some other image viewer.Notice the ASCII view in the lower right paneof ProDiscover. This shows the image bytes.JPEG images begin with a header including theASCII text 'JFIF', as shown below.
Double-click the puppy file and examineit in Photo Viewer and in ASCII view.
Using Gallery View
In the upper right pane of ProDiscover,right-click the puppy file and click'Gallery View.This is similar to the way WindowsExplorer displays folder contents.
Scroll down to see the thumbnail imagesof the two JPG files,as shown below.
Viewing Deleted Files
In the left pane of ProDiscover, click'Deleted Files'. Two files appearin the upper right pane,as shown below.Double-click the gun image. It opens inPhoto Viewer. As you can see, ProDisdcoverwas able to completely recover this file, includingthe file name.
Double-click the hackers-manifesto.docx file.
It opens in your DOCX viewer, as shown below.
Viewing All Files
In the left pane of ProDiscover, click'All Files'.A box pops up saying 'CAUTION:...that may take some time tocomplete...'. Click Yes.
This is probably the friendliest view in ProDiscover.As shown below, both active and recovered filesare shown as convenient icons,as shown below.
Viewing the Physical Drive in Cluster View
Most of the time, you can find what you need usingContent View. However, if you want to getright down to the raw bytes on the disk,you can use Cluster View.In the left pane of ProDiscover,in the 'Cluster View' section,click the plus signto expandImages.
Double-click C:UsersstudentDesktopp15p15.dd
In the top right pane,the physical drive is shown in 'Cluster View'--agrid of colored rectangles,as shown below.
Click the first red rectangle, cluster 0. In the lower rightpane, notice that it starts at address 0,as shown below.
On your keyboard, press the right-arrow key tomove to the next cluster, cluster 1.
Cluster 1 starts at address 200,as shown below.
Move right through the next few clusters tosee the pattern. Each cluster is 200 bytesin size. The 200 is in hexadecimal, so it's512 bytes in decimal. These so-called'Clusters' are actually Sectors, becauseat the direct physical level we are using,the disk has no concept of 'Clusters'.
Click the first red rectangle again to selectCluster 0. This is thefirst cluster on the disk--the Master Boot Record.
In the lower right pane, scroll down to find thecharacteristic readable text always seen in theMBR: 'Error loading operating system',as shown below.
Saving a Screen Image
Make sure your screen shows these two items:- YOUR NAME in the title bar of ProDiscover
- 'Error loading operating system' in the lowerright pane.
Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE TO GET FULL CREDIT!
Open Paint and paste in the image.
Save the image with the filename 'Your Name Proj 15b'. Use your real name, not the literal text 'Your Name'.
Viewing the Logical Drive in Cluster View
In the left pane of ProDiscover,in the 'Cluster View' section,click C:.In the top right pane, click the first rectangle toselect Cluster 0. Look at the lower rightpane--this cluster starts at address zero,as shown below.
Notice that this address is relative to the startof the C: partition, so it is not the sameas the physical sector 0 that containsthe Master Boot Record.
Notice the colors: the green clusters are 'Used'--thatis, they contain active data. The blue clusters are'Unused' and may contain latent data.
On your keyboard, press the right-arrow key tomove to the next cluster, cluster 1.
Cluster 1 starts at address 1000,as shown below.
Move to the right a few more times to see thepattern: the clusters are all 1000 bytes insize now. In Hexadecimal, that's 4 KB,the usual cluster size for an NTFS partition.
Click the first red rectangle again to selectCluster 0. This is thefirst cluster on the partition--the Partition BootSector.
In the lower right pane,in the top row, find the characters NTFS,as shown below. This, obviously, indicatesthat the partition is formatted with theNTFS file system.
Saving a Screen Image
Make sure your screen shows these two items:- YOUR NAME in the title bar of ProDiscover
- 'NTFS' in the lowerright pane.
Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE TO GET FULL CREDIT!
Open Paint and paste in the image.
Save the image with the filename 'Your Name Proj 15c'. Use your real name, not the literal text 'Your Name'.
Turning in your Project
Email the images to cnit.121@gmail.com with the subject line:Proj 15 from YOUR NAMESources
http://www.ntfs.com/ntfs-system-files.htmLast Modified: 4-7-14 1:16 PM
Video Summarizing the Problem
Response from Creator of ProDiscover
I notified Chris Brown privately, and he responded withthis message within 2 days. I really appreciate hisfast and intelligent reply!I don't completely understand the explanation--it doesn'tseem like this is the whole problem. But I'll bevery interested tosee the updated version and test it.
We have reviewed and tested the issues you reported. The first issue is problem with reading first two clusters in FAT12 partitions. In FAT12, cluster numbers start with 2, the 0th cluster being the boot information and the first cluster is directory structure. We were not handling them properly in that we were only reading first 512 bytes (one sector) of these group of sectors and displaying information. We have fixed this issue by handling reading logic for the first two clusters.The issue with the logical floppy secure wipe was that we are using a third party algorithm to erase logical disks, to be DoD compliant for logical secure wipes. This 'canned algorithm' is creating problem. Suppose, a file of 512 bytes is saved, then it occupies more than one sector on the disk. The algorithm we were using is only erasing 512 bytes. We have corrected this and will round the file size to the cluster boundary, which will fix the problem. BTW, the logical secure wipe is an old concept (as old as floppy disks) of writing random data to a logical file system. This process is only provided for DoD spec requirements and is not recommended for use in Forensics. I would always recommend wiping a disk at the physical level with a known pattern. This process ensures that you wipe any unallocated/slack space ad is visually verifiable.
What Is Prodiscover Basic
Thank you for taking the time to report these issues. They are both corrected and will release with the next product update.
Christopher L. T. Brown, CISSP, DFCP
Technology Pathways LLC
Founder & CTO
Details of Other Tests
Vendor Notification
Cluster Contents Incorrect
I am using a floppy disk image from honeynet:I am using Windows 7 in a Fusion virtual machine,on a Mac OS X host.
I downloaded it, verified the MD5, and unzipped it.
Here's the MD5 hash of the unzipped image.dd raw file:
I started ProDiscover Basic and loaded the image.dd file.
Here's the version of ProDiscover I used:
I viewed the image.dd file in Cluster view, which showsthe raw data in hex.
Here's the first sector--the MBR:
Here's the second sector--the start of the FAT.It begins with the three bytes F0 FF FF, as explainedhere:
This article tells me to expect the second copy of the FATin sector ten (0A in hex):
But this is what ProDiscover shows in sector A--theF0 FF FF is not there!
I tried a Search to find it:
The results say it should be in cluster A.

What's going on? I opened the original image.ddfile in HxD, a simple hex editor.
Here's sector 1, starting with the F0 FF FF:
Here's sector 10, starting with the F0 FF FF:
HxD also shows that all the sectors between 1 and 10 areempty--filled with 00 bytes.
But ProDiscover shows them filled with data,like this:
What's going on? What am I doing wrong?
Failure to Wipe Floppy Disk
I made a new empty .flp filelike this:This procedure was recommended here:
I connected the virtual floppy to aVMware Windows 7 machine, formatted the floppy,and filled it with text files containing manyrepeats of the word 'SPAM':
HxD shows the SPAM on the floppy:
I used ProDiscover Basic's 'Tools', 'Secure Wipe'function:
I expected the disk to be zeroed, but that'snot what ProDiscover did.
The MBR is still there:
The first FAT contains the F0 FF FF mark, but nothingelse:
The second FAT also contains the F0 FF FF mark, but nothingelse:
The root directory still contains most of anold filename 'SPAM.TXT':
This might seem like a small problem, but it'snot! The 'Secure Wipe' did not eraseall the data, it just overwrote the active data.Here's what ProDiscover did to thecontents of the SPAM files:
Now let's test this using a floppy diskwith a corrupted FAT, which I got here:
This floppy contains data of a potentiallysensitive nature.
Here's some sensitive text:
Here we see the end of a JPGimage, with the end-of-file mark FF D9,followed by a password:
(I redacted the image to avoid interfering withstudents doing the Honeynet challenge.)
I ran the ProDiscover 'Secure Wipe'on this disk, and here's the result:
The text has been overwritten:
But the other data remains on the disk:
(I redacted the image to avoid interfering withstudents doing the Honeynet challenge.)
This is not a proper forensic wipe at all!
Using Windows XP and a Real Hard Disk
I tested this using a real computer, not a virtualmachine, running Windows XP, and using a realhard disk, not a floppy disk.I made an 8 MB FAT-16 partition on the disk:
I filled it with SPAM:
It's almost completely full:
The directory structure for FAT-16 shows thatthe starting cluster is at an offset of0x1a, starting from the first characterin the filename:
Here's the directory, viewed in the HxD hexeditor.
The directory entry for theSPAM.TXT file starts at byte 10080 withthe file name.
Bytes 1009A and 1009B contain the addressof the first cluster. Right now they hold02 00.
In the hex editor, I changed byte1009A to 00. This creates an incorrectcluster number of 00 00.
I made a new project in ProDiscover and addedthe physical hard drive.
ProDiscover now shows sector 2 filled with SPAM,which is incorrect.
Here's the sector that contains the directory.ProDiscover incorrectly reports it as full of SPAM.
Here is HxD, showing the correct contents ofsector 2 (all zeroes):
Here's the actual directory on the disk.It's not full of SPAM, of course.
Thanks to 'var x' for help with the hardware.

Downloadable Test Images
I made some images anyone can use to seethis problem, and to test the next versionwhen it comes out.To use them, do these three steps:
1. Download & Extract
Download the file you prefer(DD or E01 format) and extract with 7-zip.Each archive contains a text file with hashesto verify accuracy, if you wish to.
2. View in ProDiscover
Open the image in ProDiscover and look at the contentsof cluster 3:3. View in Another Tool
Open the image in HxD or any other tool and look at the contentsof cluster 3. You can easily see that the contents are notthe same:FAT32 Test Images
How These Images Were Made
I made a FAT32 partition, copied a textfile to it, and zeroed its first cluster addressin the FAT. I captured an image of thatwith FTK Imager.Then I converted that disk to NTFS with theWindows command-line tool CONVERTto create the NTFS sample partition. I acquired itwith FTK Imager.
Thanks to 'varx' for the idea to CONVERT the disk.
Vendor Notification
I emailed the vendor on 1-23-13 about problem #1.Posted by Sam Bowne, 8:10 PM, Jan 23, 2013Problem #2 added 8:45 am, Jan 24, 2013
Item #3 added 4:44 PM Jan 24, 2013
Prodiscover Basic Forensics Software
Video and vendor responses added 4:33 pm Jan. 25, 2013
Prodiscover Basic Edition
Images redacted 5:28 pm Jan. 25, 2013
Prodiscover Basic Features
Image files added 1-26-13 9:18 pm